EVPN technology is improved in order to eliminate some limitations of VPLS. RFC7432 gives large details of Ethernet Virtual Private Network. EVPN simply provides to carry mac address table in network environment from PE router to another PE routers, which are called here VTEPs.To do this, there are some requirements such that MP-BGP and LDP/RSVP in traditional network. One of the main benefit of EVPN is to decrease BUM traffic in datacenter network. In EVPN, you create a table that includes mac addresses and loopback IP. It is simple a database. Then, PE routers advertise those mac tables each other. With this, PE routers say “those mac address on me and send your layer 2 traffic to my loopback address to reach those mac adresses”. Thus, each routers hold mac address tables.
In traditional network, this forwarding is done by MPLS. But we will learn today how EVPN-VXLAN is working without MPLS environment. Is it possible to connect to datacenters as layer 2 if only using BGP? Yes it is possible.
In previous post, we have learned VXLAN in Arista. There was a CVX for central management of mac address table in that post. But now, there is no CVX. Mac address will be carried via BGP and forwarding will be done VXLAN tunneling instead of MPLS.
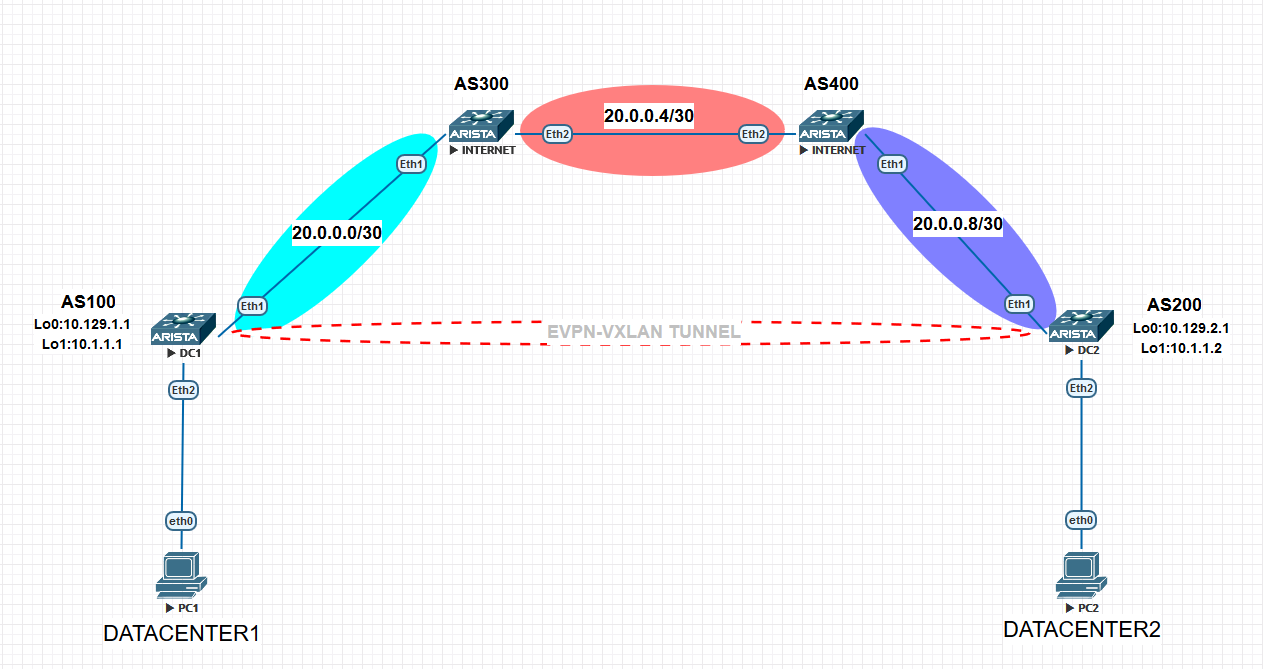
In this post, we will connect two different datacenters whose uplinks are connected to internet and this internet not under our control. This connection will be layer 2 and PCs will ping each other in same broadcast domain even if there is another ISP in topology.
Establishing Environment for EVPN
First of all, we will build BGP environment for EVPN. All routers will communicate EBGP each other. DC1 and DC2 will advertise their “loopback0 “ address each other to establish EVPN neighbor. This EVPN neighborship will use to carry mac address table. In BGP configuration, ebgp-multihop feature must be used since they are not directly connected. In addition, we will activate the neighborship under address-family evpn not IPV4 or IPV6. So, configure
no bgp default ipv4-unicast under global BGP. Send-community is required in order to advertise route distinguisher/target information.
[huge_it_gallery id=”48″]
Secondly, VLAN will be created and VXLAN configuration will be applied. Here, we create VNI in both DC1 and DC2 devices. This VNI has to be same but VLANs not. In this topology, for VXLAN we used source IP as loopback 1 because of redundancy purposes. If there were two switches in each location, we would advertise same loopback1 IP address from both switches to provide redundancy. Because loopback 1 is VTEP IP and you will see this IP in opposite device to reach mac address.So, loopback 1 is used as next-hop for mac-address. In redundant topology, reachability to VXLAN source IP, which is loopback1 here, is critical.But in this post, there is no redundancy, even so we used loopback1.
[huge_it_gallery id=”49″]
As a result, we provided VXLAN header insertion to packet and we will advertise this mac and IP information via BGP EVPN. Now, we created tunnel between VTEPS over internet without MPLS, only IP reachability.So, PC1 and PC2 can ping each other in same VLAN100.
[huge_it_gallery id=”50″]
[huge_it_gallery id=”51″]
Configuration Example for EVPN in DC1 and DC2
DC1
service routing protocols model multi-agent
router bgp 100
router-id 10.129.1.1
no bgp default ipv4-unicast
neighbor 10.129.2.1 remote-as 200
neighbor 10.129.2.1 update-source Loopback0
neighbor 10.129.2.1 ebgp-multihop 4
neighbor 10.129.2.1 send-community
neighbor 10.129.2.1 maximum-routes 12000
neighbor 20.0.0.2 remote-as 300
neighbor 20.0.0.2 maximum-routes 12000
!
vlan 100
rd 10.129.1.1:100
route-target import 200:10100
route-target export 100:10100
redistribute learned
!
address-family evpn
neighbor 10.129.2.1 activate
!
address-family ipv4
neighbor 20.0.0.2 activate
network 10.1.1.1/32
network 10.129.1.1/32
interface Vxlan1
vxlan source-interface Loopback1
vxlan udp-port 4789
vxlan vlan 100 vni 10100
DC2
service routing protocols model multi-agent
router bgp 200
router-id 10.129.2.1
no bgp default ipv4-unicast
neighbor 10.129.1.1 remote-as 100
neighbor 10.129.1.1 update-source Loopback0
neighbor 10.129.1.1 ebgp-multihop 4
neighbor 10.129.1.1 send-community
neighbor 10.129.1.1 maximum-routes 12000
neighbor 20.0.0.9 remote-as 400
neighbor 20.0.0.9 maximum-routes 12000
!
vlan 100
rd 10.129.2.1:200
route-target import 100:10100
route-target export 200:10100
redistribute learned
!
address-family evpn
neighbor 10.129.1.1 activate
!
address-family ipv4
neighbor 20.0.0.9 activate
network 10.1.1.2/32
network 10.129.2.1/32
interface Vxlan1
vxlan source-interface Loopback1
vxlan udp-port 4789
vxlan vlan 100 vni 10100
Beneficial Commands
show bgp evpn summary
show bgp neighbors 10.129.1.1 evpn routes
show bgp evpn route-type mac-ip
show vxlan address-table
Note:You can find more information about this in below UDEMY link.
Merhaba Mahmut Bey,
Paylaşımlarınızı beğeni ile takip ediyorum, emeğinize sağlık.
İyi çalışmalar dilerim.